Security Responsibility
Leadership & Strategy
Spearheading red team operations to enhance cyber resilience against Advanced Persistent Threats (APTs) through cutting-edge offensive security techniques.
Offensive Security
Conducting comprehensive penetration testing, cloud security assessments, and developing advanced exploit techniques to identify and mitigate potential vulnerabilities.
Secure Architecture
Implementing robust DevSecOps practices, ensuring compliance with ISO 27001:2022, and building secure architectures that protect against emerging cyber threats.
Key Responsibilities
Assessing Security
System & Server Security
Network Security
IoT Security
Cloud Security
Endpoint Security
Application Security
Standardization & Compliance
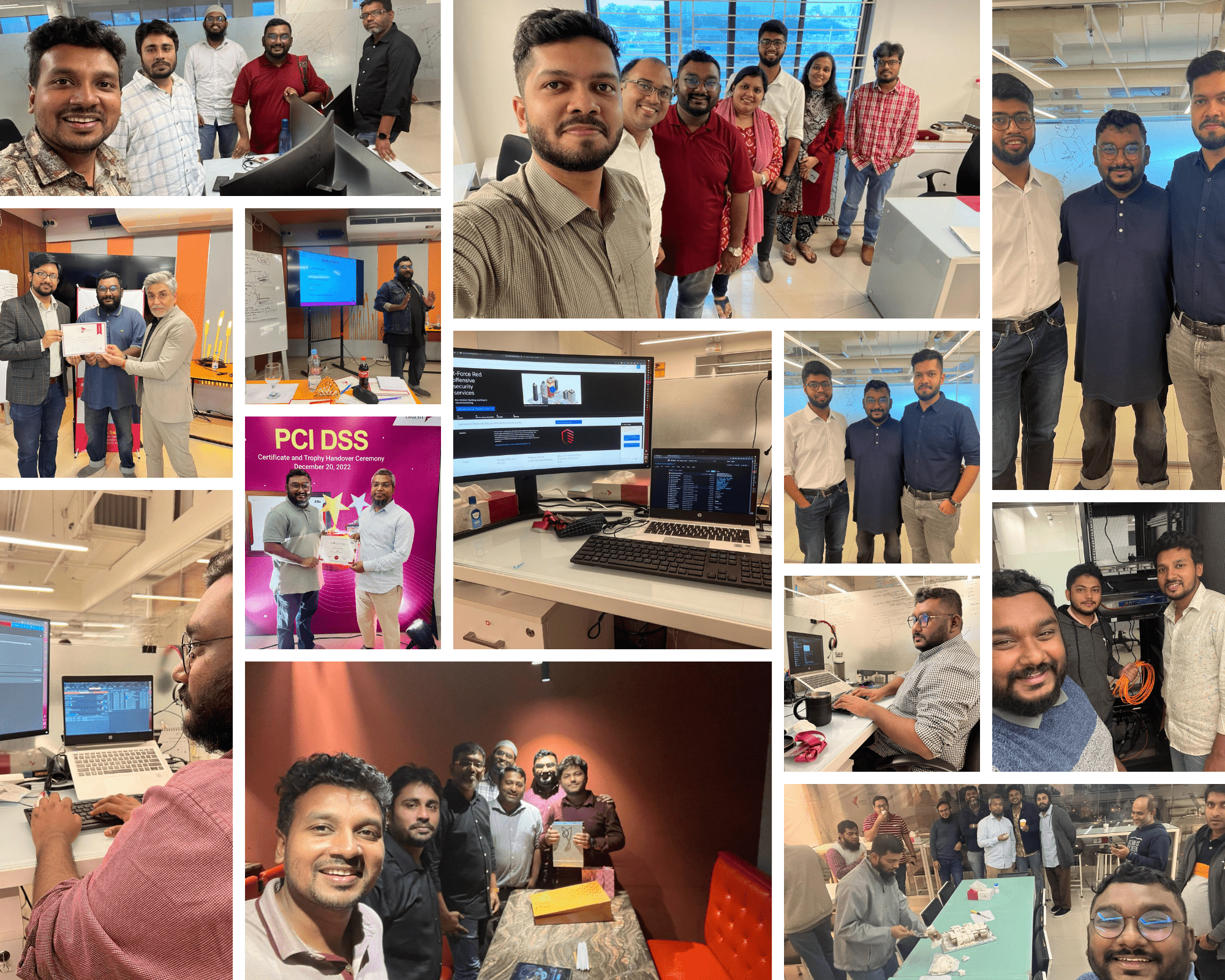
Projects Delivered
Vulnerability Management Introduced
Initiation
Establishing initial security baseline, defining vulnerability management framework and scope.
Remediation
Systematic prioritization and resolution of identified security vulnerabilities and risks.
Monitoring & Periodic Check
Continuous surveillance, periodic assessments, and adaptive security strategy refinement.
Mobile Application Security
Reverse Engineering
Deep dive into mobile app architecture, uncovering internal mechanics and potential vulnerabilities.
ID and Manifest Analysis
Comprehensive examination of application identifiers and manifest files for security insights.
Source Code Analysis
Meticulous line-by-line review to identify and mitigate potential security weaknesses.
Automated Analysis
Advanced automated scanning to detect and flag potential security vulnerabilities efficiently.
Report Standardization
Vulnerability Assessment
A detailed analysis of security weaknesses in systems, with prioritized recommendations for remediation.
Penetration Testing
A summary of simulated attacks identifying exploitable vulnerabilities, with insights to strengthen defenses.
Mobile Application
Highlights security flaws in mobile apps, focusing on vulnerabilities in code and data handling.
IAM Assessment
An evaluation of Identity and Access Management processes to identify access control gaps and improve data protection.
Identified Vulnerabilities
File Upload Vulnerability
Risks associated with unrestricted file uploads that can lead to remote code execution.
Broken Access Control
Vulnerabilities that allow unauthorized access to restricted resources or functionality.
Injection
Vulnerabilities that allow malicious code injection into application inputs.
WebRTC Vulnerability
Security risks in WebRTC implementations that can expose network information.
JWT-based Vulnerabilities
Security weaknesses in JSON Web Token implementation and validation.
Local File Inclusion
Vulnerabilities that allow unauthorized access to local files on the server.
Data Exposure Vulnerabilities
Risks of sensitive data being unintentionally exposed or leaked.
Others
Additional miscellaneous vulnerabilities not covered in specific categories.
Cyber Resilience
Proactive Strategy
Implementing advanced threat detection and response mechanisms.
Attack Simulation
Continuous breach and attack simulations to identify vulnerabilities.

Process, Policy & Guideline
Web Application & API Penetration Testing
Mobile Application Penetration Testing
End-Point Penetration Testing
API Security Guideline
Overall Security Guideline
Solution Go-Live Guideline
IAM Guideline
Vulnerability Assessment & Penetration Testing Policy
Solution Security Process
Exploitation Innovation
File Upload Innovation
Created a JavaScript application demonstrating server-side JS rendering in file upload vulnerabilities.
Cyber Kill Chain
Developed a PoC .vbs file to conceptualize weaponization of the Cyber Kill Chain.
WebRTC Tool
Built IceWatch to demonstrate WebRTC credential exploitation.
JWT Exploitation
Cracked JSON Web Tokens to identify weak signing keys for account impersonation.
File Inclusion
Discovered and documented Local File Inclusion vulnerabilities in server endpoints.
Brute Force
Designed automated scripts for testing login forms and SSH credential security.
Injection Exploitation
Exploited injection vulnerabilities using emoji HTML image tags for PDF linking and IP tracking.
Cookie Monster
Created CookieMonster, a Selenium-based tool for local storage manipulation and cookie theft.
Decreasing Dependency
Achieved significant reduction in reliance on external security assessment vendors.
IoT Assessment
Wireless Network
Printers
PDUs
CCTV Camera
SDLC Rollout
Secure Development Lifecycle Implementation
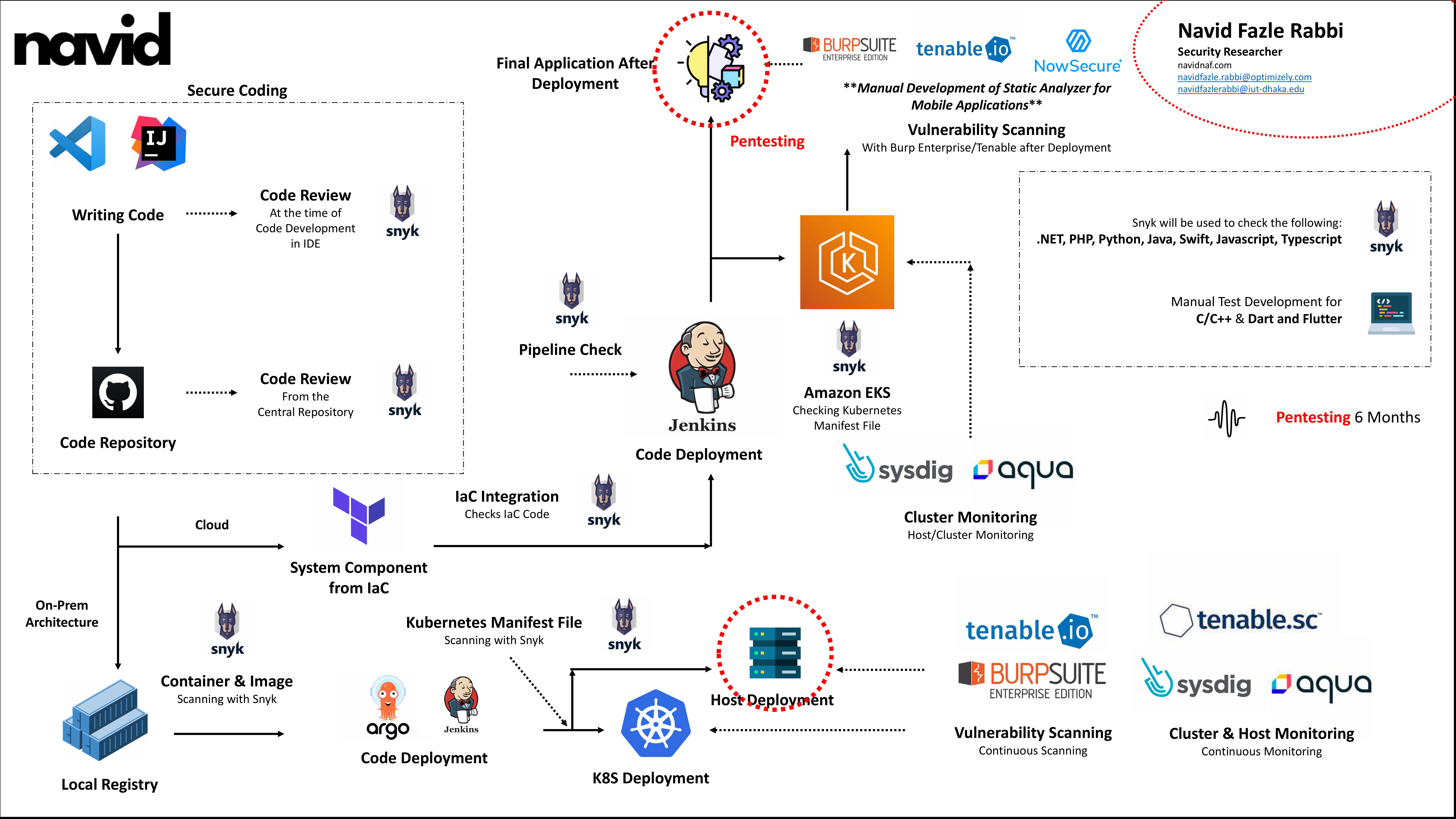
Demo Secure Development Lifecycle Plan
Compliance & Frameworks






Collaboration Projects



















Redesigning Recruitment
The Start
Stream Lining On-Boarding Process
Domain Centric Assessments
Exploring Current Security Mindset
Real-time Competitive Challenges
Initial Screening
Shortlisted candidates were considered based on their interests and experience.
On-Boarding Assessment
Candidates were put through a rigorous assessment that included tasks based on real-time security scenarios.
Assessment Walkthrough
Candidates presented their work in an online session where they were asked a variety of questions on the area.
Final Interview
The candidates were brought in for a final interview after completing the arduous screening process.
On-Boarding
Finally, the picked were on-boarded.
The Upgrade
Upgraded to a Dockerized Environment
Introduced more focused challenges
Increased difficulty level
Enabled full-time support
Initial Screening
Shortlisted candidates were considered based on their interests and experience.
Initial On-Call Assessment
Candidates were taken phone call interviews and candidates were shortlisted.
Dockerized Assessment
A 36-Hour long assessment was taken to challenge the candidates in timely focused situations.
On-Site Interview
Shortlisted Candidates from Phase 4 were brought on-site for hour long interview sessions.
Final Interview
The candidates were brought in for a final interview after completing the arduous screening process.
On-Boarding
Finally, the picked were on-boarded.
Thank You for Visiting!
Your interest in my cybersecurity journey at bKash means a lot. Feel free to connect with me for any security-related discussions or collaborations.